Managing App Templates
This article describes the administrative actions needed to configure App templates in CloudShell that are based on a cloud provider resource. For additional information, see Apps Overview.
In this article:
Viewing App templates
In the Apps page, you can view the App templates you are permitted to access.
To view existing App templates:
- In the Manage dashboard, in the left sidebar, click Apps.
The Apps page is displayed, listing the App templates that were previously added to CloudShell.
You can use the toolbar to sort the App templates according to Name or date of modification, and to filter them according to a specific Category or Domain.
Adding App templates
When adding a new App template, you need to configure the settings of the virtual machine and application you want to deploy. To add App templates, at least one cloud provider resource must be defined. To define private cloud provider resources, see Private Cloud Provider Support in CloudShell, and for public cloud providers, see Public Cloud Provider Support in CloudShell.
If your CloudShell deployment includes multiple sites, it is recommended to configure the deployment process of the App to be carried out in the domain that is physically closest to the cloud provider. For additional information, see Managing Private Cloud Apps in Domains or Managing Public Cloud Apps in Domains.
- By default, all public cloud Apps of the same type in the same sandbox are deployed within the same subnet and therefore are connected to each other and isolated from other sandboxes. However, using the Subnet service, blueprint designers can set up multiple subnet networks in the sandbox, instead of having one default subnet for all the Apps of the same cloud provider. For details, see Subnet Connectivity.
- Public cloud App deployment requires the management network and subnet(s) to be prepared in advance as part of the sandbox Setup process. CloudShell's out-of-the-box Setup process does this. However, the blueprint must include at least one public cloud App to initiate the Setup script's connectivity preparation process for deployment in that public cloud.
To add a new App template:
-
Click + Add.
The Create New App wizard is displayed.
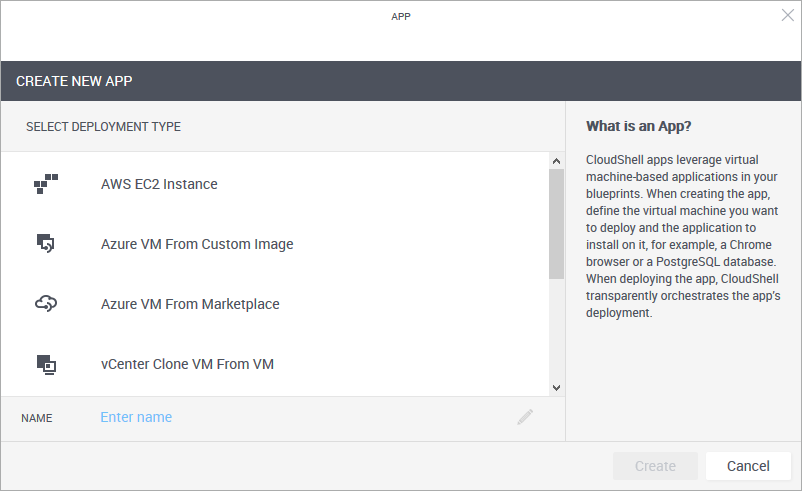
- From the Select Deployment Type pane, select the desired deployment type. For example, "vCenter VM From Template" deploys a vCenter virtual machine from a template while "AWS EC2 Instance" deploys an AWS EC2 instance from an AMI image.
-
Enter a Name for the App template.
Note: The App template's name has a limit of 100 characters and can only contain alpha-numeric characters, spaces, and the following characters: | . - _ ] [
-
Click Create.
The App template is created and the App wizard's General page is displayed.
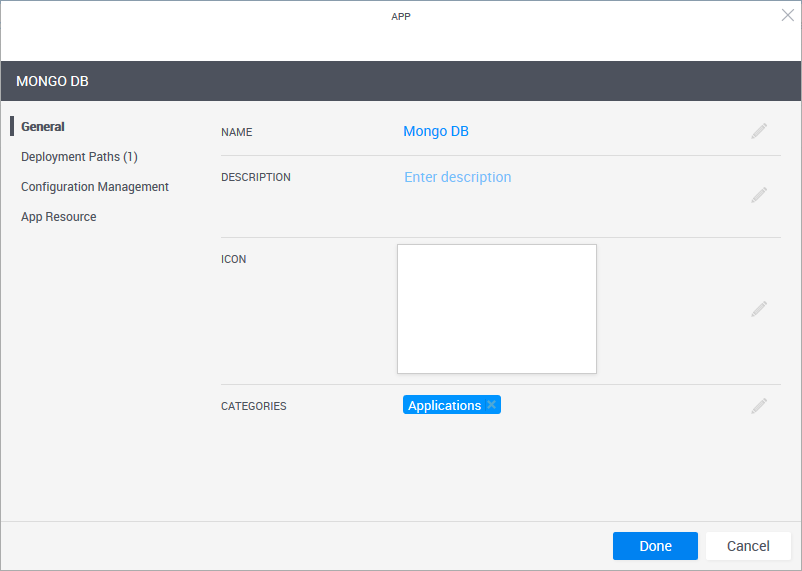
-
In the General page, define the App template's display settings and category.
 More...
More...
Field Required Description Name Required App name that is displayed in the catalog. Description Optional Description of the App. Icon Optional Add an image to the catalog definition. The recommended size for the image is 190x120 pixels (image size is limited to 400x400 pixels or 200 KB). Categories Optional Service categories are a method to classify Apps. The Apps are displayed in the Add App / Service side pane in the blueprint and sandbox diagram, arranged in categories. Only users who are permitted to view the category can access the App. Apps without a category are not displayed.
By default, the Applications category is selected.
Select a category from the dropdown list. You can select additional categories. Examples of categories are: applications, networking and VLAN.
Notes:- The category must be associated with the domain in which the required cloud provider resides. For information about domain categories, see Managing domain categories.
- It is recommended to use up to a 2-level hierarchy when organizing the Add App / Service catalog (i.e. root and sub-category).
- In the Add App / Service side pane, Apps are displayed in the root category only. This includes services associated to sub-categories.
-
In the left pane, click Deployment Paths and configure the App template's deployment path.
 More...
More...
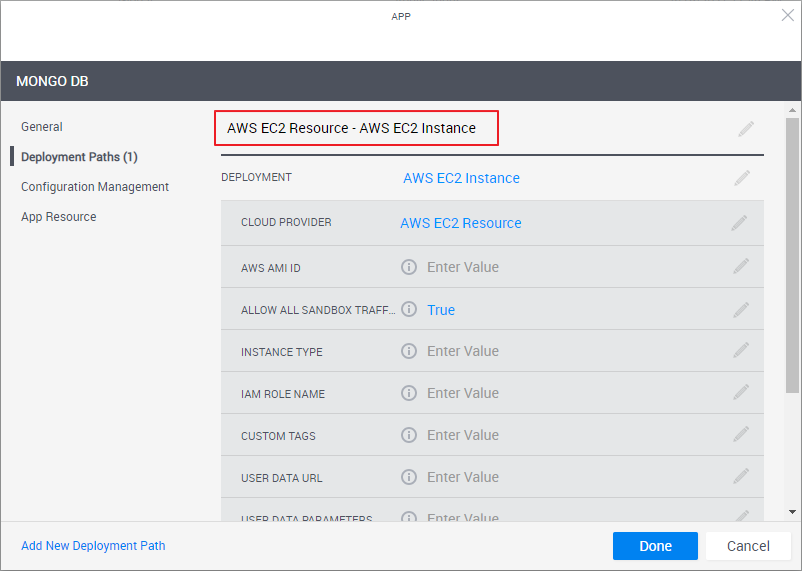
A deployment path consists of (1) the selected deployment type (the method to be used to deploy the VM, for example, from a vCenter VM template or AWS AMI image, (2) the VM’s settings such as storage size, CPU and image file, and (3) the CloudShell cloud provider resource that enables CloudShell to access the cloud provider and deploy the VM on it.
Note the deployment path's name (highlighted in the image below). The path's name is dynamic and consists of the selected Cloud Provider resource and Deployment type. You can change the name of the path by clicking the field.
-
From the Deployment drop down list, select the deployment type.
The selected deployment type's attributes are displayed.
-
Enter the required information.
-
For AWS EC2 Instance attributes,
 more...
more...
Cloud Provider Name of the AWS EC2 cloud provider resource to be used AWS AMI ID AWS AMI ID to launch the instance from. For example, "ami-6869aa05".
Note: The AMI must be accessible in the selected cloud provider's AWS region.
Instance Type AWS EC2 instance type. The instance type determines the CPU, memory, storage and networking capacity of the instance. For example, "t2.large".
Leave empty to use the default instance type specified in the AWS EC2 resource.
Allow All Sandbox Traffic Determines if the App allows inbound traffic from all other AWS EC2 Apps in the sandbox. If set to False, the instance will be isolated. Access from specific Apps or subnets can be defined using the Inbound Ports attribute or API.
Note: By default, this attribute is True. This means that all access is allowed to all ports from all Apps in the sandbox and all ports are open for traffic within the sandbox.
IAM Role Name (Optional) Name of the IAM role to associate to the App's instance. If the role does not exist, or there are other issues with launching the instance with the role, App deployment will fail. Custom Tags Custom tags to be set on CloudShell-deployed AWS EC2 instances for billing, like the details of the project or team that deployed the instance.
For multiple tags, specify a comma-separated list of the key-value pairs. For example:
tag_name1:ec2_instance,tag_name2:ec2_instance2User Data URL (Optional) URL to the script to execute (PowerShell, bash, sh, etc.). User Data Parameters (Optional) Parameters to pass to the user data script. For example, specifying
param1 param2will result in the command running as follows:./file.sh param1 param2Inbound Ports Semi-colon separated list of ports and protocols to open for inbound traffic. Note that by default all ports are open for traffic between AWS EC2 App instances within the sandbox, but this can be changed using the Allow All Sandbox Traffic attribute.
In addition, all outbound traffic is allowed.
The syntax is:
port[single/range]:protocol[tcp(default)/udp]For example: "80;443:tcp;200-220:udp".
Note: If not specified, the protocol defaults to TCP.
Tips:
- To allow QualiX in-browser connections to the VM from the sandbox, include port "22".
- To set more specific security groups, it is recommended to use the TestShell API's
SetAppsSecurityGroupmethod instead. Unlike the Inbound Ports attribute, it enables you to define different port settings per subnet and allow inbound access to specific source CIDRs. For additional information, see SetAppSecurityGroups Code Example.
Public IP Options Enables access to the instance from the internet. Options are:
- No Public IP - default option
- Public IP (single subnet) - (for Apps connected to a single subnet [private or public]) allocates a public IP
-
Elastic IPs - (for Apps connected to multiple subnets) allocates an elastic IP for the App in each of the public subnets that it is connected to
Note: In AWS EC2 Apps, this setting is mandatory if the App is connected to more than one network (private or public).
Private IP When the VPC is in static mode (defined on the AWS EC2 cloud provider resource's VPC Mode attribute), this attribute is used to set a static private IP for the deployed App.
To set a static private IPs in multi-subnet mode, specify a json string that maps the subnet request CIDR to the requested static private IP. For example: {"10.0.0.0/28": "10.0.0.6"}
-
For Azure VM From Custom Image attributes,
 more...
more...
Cloud Provider Name of the Azure cloud provider resource to be used VM Size (Optional) Size of the Microsoft Azure computing resources, including CPU, memory and networking capacity of the VM. Leave it empty to use the default VM Size that was set in the cloud provider resource. For example: “Standard_A0”.
For Azure Apps that will run configuration management operations, specify a VM size of Basic_A2 or larger.
For additional information, see the Azure help page Sizes for virtual machines in Azure or use Azure CLI to get a list of your region's supported sizes.
Disk Size (Optional) VM's disk size in GB. For example, “17” or “35”.
If you leave it empty, CloudShell will determine the disk size according to the App's VM Size.
Wait for IP Determines if the App deployment process waits for the VM to get an IP. Default is False.
Add Public IP Set to True to use a public IP address to communicate with the VM from outside the virtual network.
In most cases the public IP address is associated with the VM until the VM is stopped or terminated, after which the IP is no longer available. To ensure that the IP is available to your subscription at any time, reserve it by setting the Public IPType attribute to Static.
Allow All Sandbox Traffic Determines if the App allows inbound traffic from all other Azure Apps in the sandbox. If set to False, the App's VM will be isolated. Access from specific Apps or subnets can be defined using the Inbound Ports attribute or API.
Note: By default, this attribute is True, and access is allowed to all ports from all Apps in the sandbox. By default, all ports are open for traffic within the sandbox.
Extension Script File / Configuration (Optional) Custom extension script (PowerShell, Python, batch, etc.) to execute on the deployed VM.
- Extension Script File: Raw URL of the script file
-
Extension Script Configuration: Space-separated value containing the tool to be used to execute the script, such as Python or PowerShell, the script's file name and extension, and any inputs that need to be passed to the script. For example:
python my_script.py input1input2Notes:- For non-PowerShell scripts, the tool to be used to execute the script must be installed on the VM.
- For Linux VMs, you must specify the tool to be used. For Windows VMs, PowerShell is used by default, unless a different tool is specified.
Note: To support the execution of extension scripts, custom images created outside of Azure Marketplace must include the ProvisionGuestAgent agent. For additional information, see Virtual machine extensions and features for Windows.
Public IP Type Set to Static to ensure that the VM always uses the same public IP. By default, public IPs are Dynamic and the address associated to them may change when the VM is powered off. Inbound Ports Semi-colon separated list of ports and protocols to open for inbound traffic. Note that by default access from the management VPC is allowed and all ports are open for traffic between Azure App VMs within the sandbox, but this can be changed using the Allow All Sandbox Traffic attribute.
In addition, all outbound traffic is allowed.
The syntax is:
port[single/range]:protocol[tcp(default)/udp]For example: "80;443:tcp;200-220:udp".
Note: If not specified, the protocol defaults to TCP.
Tips:
- To allow QualiX in-browser connections to the VM from the sandbox, include port "22".
- To set more specific security groups, it is recommended to use the TestShell API's
SetAppsSecurityGroupmethod instead. Unlike the Inbound Ports attribute, it enables you to define different port settings per subnet and allow inbound access to specific source CIDRs. For additional information, see SetAppSecurityGroups Code Example.
Resource Group Resource group in which the custom image resides. Image Name Name of the custom image. The image name is listed in the Images blade of the Azure portal.
Disk Type Type of disk to use (HDD / SSD). Default is HDD.
-
For Azure VM From Marketplace attributes,
 more...
more...
Note: Every VM deployed from a Marketplace image is created with a managed disk, which is deleted when the sandbox ends.
If you want to deploy a third party application from a Marketplace image, make sure Programmatic Deployment is enabled for the image in the subscription. To enable, log in to Azure and open the Marketplace, find the image and click it, select the Want to deploy programmatically? Get started link at the bottom of the blade that appears. Then, in the Configure Programmatic Deployment blade, scroll down to the bottom, select Enable for the appropriate subscription and click Save. For additional information, see the following Azure help page: Working with Marketplace Images on Azure Resource Manager.
Cloud Provider Name of the Azure cloud provider resource to be used VM Size (Optional) Size of the Microsoft Azure VM. This parameter determines the CPU, memory and networking capacity of the VM. Leave it empty to use the default VM Size that was set in the cloud provider resource. For example: “Standard_A0”.
For Azure Apps that will run configuration management operations, specify a VM size of Basic_A2 or larger.
Disk Size (Optional) VM's disk size in GB. For example, “17” or “35”.
If you leave it empty, CloudShell will determine the disk size according to the App's VM Size.
Add Public IP Set to True to use a public IP address to communicate with the virtual machine from outside the virtual network.
In most cases the public IP address is associated with the VM until the VM is stopped or terminated, after which the IP is no longer available. To ensure that the IP is available to your subscription at any time, reserve it by setting the Public IP Type attribute to Static.
Wait for IP Determines if the App deployment process waits for the VM to get an IP. Default is False.
Extension Script File / Configuration (Optional) Custom extension script (PowerShell, Python, batch, etc.) to execute on the deployed VM.
- Extension Script File: Raw URL of the script file
-
Extension Script Configuration: Space-separated value containing the tool to be used to execute the script, such as Python or PowerShell, the script's file name and extension, and any inputs that need to be passed to the script. For example:
python my_script.py input1input2Notes:- For non-PowerShell scripts, the tool to be used to execute the script must be installed on the VM.
- For Linux VMs, you must specify the tool to be used. For Windows VMs, PowerShell is used by default, unless a different tool is specified.
Public IP Type Set to Static to ensure that the VM always uses the same public IP. By default, public IPs are Dynamic and the address associated to them may change when the VM is powered off. Inbound Ports Semi-colon separated list of ports and protocols to open for inbound traffic. Note that by default access from the management VPC is allowed and all ports are open for traffic between Azure App VMs within the sandbox, but this can be changed using the Allow All Sandbox Traffic attribute.
In addition, all outbound traffic is allowed.
The syntax is:
port[single/range]:protocol[tcp(default)/udp]For example: "80;tcp:443;udp:200-220".
Note: If not specified, the protocol defaults to TCP.
Tips:
- To allow QualiX in-browser connections to the VM from the sandbox, include port "22".
- To set more specific security groups, it is recommended to use the TestShell API's
SetAppsSecurityGroupmethod instead. Unlike the Inbound Ports attribute, it enables you to define different port settings per subnet and allow inbound access to specific source CIDRs. For additional information, see SetAppSecurityGroups Code Example.
Disk Type Type of disk to use (HDD / SSD). Default is HDD. Image Publisher Define the VM image's Publisher, Offer and SKU.
Note: The Publisher, Offer and SKU must exist in the Azure region where the VM will be deployed.
For typical image properties, see the following Azure help pages: Linux VM images and Windows VM images.
Image Offer Image SKU Allow All Sandbox Traffic Determines if the App allows inbound traffic from all other Azure Apps in the sandbox. If set to False, the App's VM will be isolated. Access from specific Apps or subnets can be defined using the Inbound Ports attribute or API.
Note: By default, this attribute is True, and access is allowed to all ports from all Apps in the sandbox. By default, all ports are open for traffic within the sandbox.
-
For vCenter Clone VM From VM attributes,
 more...
more...
Cloud Provider Name of the vCenter cloud provider resource to be used vCenter VM Full path to the VM that will be used to clone a new VM, relative to the datacenter. For example: My-Folder/My-VM Behavior During Save (optional)
(Applies to the Save and Restore paid add-on) The VM's state while the sandbox is being saved. Options are Remain Powered On and Power Off.
- Remain Powered On: The VM will remain powered on during the saving state.
-
Power Off: If the VM was powered on before the sandbox entered the saving state, the VM will shut down (power off) for the duration of the save.
Note: After save has ended, the VM returns to its state prior to saving, regardless of the behavior during the save.
Note: The value configured here overrides the configuration in the vCenter cloud provider resource, see Add VMware vCenter Cloud Provider Resource.
Saved Sandbox Storage (Applies to the Save and Restore paid add-on) During the saving process, CloudShell creates a clone of the sandbox's App VMs in this vCenter storage, which CloudShell will later use to restore the VM when the user restores the saved sandbox. See Save a Sandbox for more information.
For storage purposes, these VM clones can be stored in a different data storage than the one configured in the VM Storage attribute defined on the vCenter cloud provider resource. The storage can be either a datastore or a datastore cluster. For example: datastore1 or clustername/datastore1.
Note: The value configured here overrides the configuration in the vCenter cloud provider resource, see Add VMware vCenter Cloud Provider Resource.
-
For VCenter Deploy VM From Linked Clone attributes,
 more...
more...
Cloud Provider Name of the vCenter cloud provider resource to be used vCenter VM Full path to the VM containing the snapshot that will be used to clone a new VM, relative to the datacenter. vCenter VM Snapshot Full path to the virtual machine snapshot that will be used to clone a new VM. For example Snapshot1/Snapshot2
This snapshot should be associated with the VM defined in the vCenter VM input.
Behavior During Save (Applies to the Save and Restore paid add-on) The VM's state while the sandbox is being saved. Options are Remain Powered On and Power Off.
- Remain Powered On: The VM will remain powered on during the saving state.
-
Power Off: If the VM was powered on before the sandbox entered the saving state, the VM will shut down (power off) for the duration of the save.
Note: After save has ended, the VM returns to its state prior to saving, regardless of the behavior during the save.
Note: The value configured here overrides the configuration in the vCenter cloud provider resource, see Add VMware vCenter Cloud Provider Resource.
Saved Sandbox Storage (Applies to the Save and Restore paid add-on) During the saving process, CloudShell creates a clone of the sandbox's App VMs in this vCenter storage, which CloudShell will later use to restore the VM when the user restores the saved sandbox. See Save a Sandbox for more information.
For storage purposes, these VM clones can be stored in a different data storage than the one configured in the VM Storage attribute defined on the vCenter cloud provider resource. The storage can be either a datastore or a datastore cluster. For example: datastore1 or clustername/datastore1.
Note: The value configured here overrides the configuration in the vCenter cloud provider resource, see Add VMware vCenter Cloud Provider Resource.
-
For vCenter VM From Image attributes,
 more...
more...
Cloud Provider Name of the vCenter cloud provider resource to be used
vCenter Image Full path to the vCenter OVF image file, relative to the datacenter. For example: My-OVF-Images/Image.ovf
Notes: Path must be accessible to all execution servers. OVF tool must be installed on all execution servers.vCenter Name Name of the vCenter resource to be used vCenter Image Arguments (Optional) vCenter-specific arguments to use when deploying the virtual machine.
Example for OVF:
--allowExtraConfig --prop:Hostname=ASAvtest --prop:HARole=Standalone --prop:SSHEnable=True --prop:DHCP=True --net:Management0-0='Office LAN 41' --net:GigabitEthernet0-0='VLAN_access_101'Behavior During Save (Applies to the Save and Restore paid add-on) The VM's state while the sandbox is being saved. Options are Remain Powered On and Power Off.
- Remain Powered On: The VM will remain powered on during the saving state.
-
Power Off: If the VM was powered on before the sandbox entered the saving state, the VM will shut down (power off) for the duration of the save.
Note: After save has ended, the VM returns to its state prior to saving, regardless of the behavior during the save.
Note: The value configured here overrides the configuration in the vCenter cloud provider resource, see Add VMware vCenter Cloud Provider Resource.
Saved Sandbox Storage (Applies to the Save and Restore paid add-on) During the saving process, CloudShell creates a clone of the sandbox's App VMs in this vCenter storage, which CloudShell will later use to restore the VM when the user restores the saved sandbox. See Save a Sandbox for more information.
For storage purposes, these VM clones can be stored in a different data storage than the one configured in the VM Storage attribute defined on the vCenter cloud provider resource. The storage can be either a datastore or a datastore cluster. For example: datastore1 or clustername/datastore1.
Note: The value configured here overrides the configuration in the vCenter cloud provider resource, see Add VMware vCenter Cloud Provider Resource.
-
For vCenter VM From Template attributes,
 more...
more...
Cloud Provider Name of the vCenter cloud provider resource to be used vCenter Template Path to the vCenter template to use in the virtual machine's creation. Path is relative to the datacenter and must include the template name, for example: My-Templates/Template1 Behavior During Save (Applies to the Save and Restore paid add-on) The VM's state while the sandbox is being saved. Options are Remain Powered On and Power Off.
- Remain Powered On: The VM will remain powered on during the saving state.
-
Power Off: If the VM was powered on before the sandbox entered the saving state, the VM will shut down (power off) for the duration of the save.
Note: After save has ended, the VM returns to its state prior to saving, regardless of the behavior during the save.
Note: Setting a value in the App template’s attribute will override the value in the Behavior During Save attribute on the vCenter resource. See Add VMware vCenter Cloud Provider Resource.
Saved Sandbox Storage (Applies to the Save and Restore paid add-on) During the saving process, CloudShell creates a clone of the sandbox's App VMs in this vCenter storage, which CloudShell will later use to restore the VM when the user restores the saved sandbox. See Save a Sandbox for more information.
For storage purposes, these VM clones can be stored in a different data storage than the one configured in the VM Storage attribute defined on the vCenter cloud provider resource. The storage can be either a datastore or a datastore cluster. For example: datastore1 or clustername/datastore1.
Note: Setting a value in the App template’s attribute will override the value in the Saved Sandbox Storageattribute on the vCenter resource. See Add VMware vCenter Cloud Provider Resource.
-
-
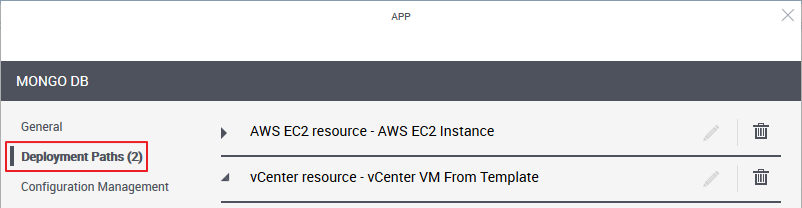
- To add additional deployment paths to the App template, click the Add New Deployment Path link at the bottom of the wizard and fill in the required information.
Note that for Apps with multiple deployment paths, the user who adds the App to the blueprint or sandbox diagram will be prompted to select the suitable deployment path to use out of the deployment paths that are based on cloud provider resources in that user’s domain.
-
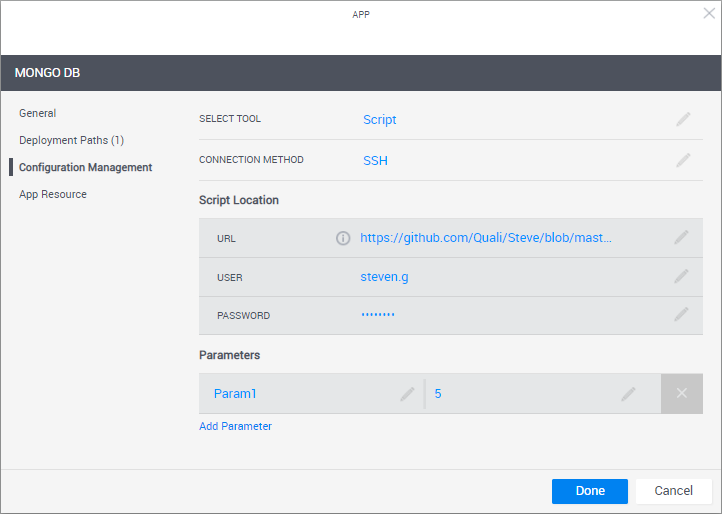
In the left pane, click Configuration Management and configure the application to be installed on the VM.
 More...
More...
 Tips:
Tips:- How to set up support for the desired configuration management tool, see Configuration Management Support in CloudShell.
- How to develop custom scripts and Ansible playbooks, including examples, see Developing Configuration Management Scripts for Apps.
Important:- To run configuration management on an Azure App, make sure the App's VM size is Basic_A2 or larger.
-
For configuration management operations, CloudShell uses an available Execution Server (for Ansible, it's a Linux Execution Server that has the Supports Ansible flag).
If the cloud provider resource has an Execution Server Selector configured, it will use that selector. If the selector is empty, CloudShell will use the selector defined in the appropriate Resource Manager Client >Configuration Services model (Ansible Configuration or Custom Script Configuration).
-
Execution Server selectors specified on the deployed App shell/resource are not used to execute configuration management operations.
Select Tool Select the application's installation and configuration tool.
- None: Do not use any Configuration Management option. Use this option if, for example, the image or template already contains the application to install.
- Script: Install the application from a custom script (PowerShell, bash or sh).
-
Ansible: (Intended for customers who are already using Ansible) Install and configure the application using an Ansible playbook.
Note: The playbook runs once during the Setup phase for all of the sandbox's Apps that use that playbook, after CloudShell has finished deploying their VMs. This is done both to improve performance and support cross-server logic where multiple applications need to be installed and configured in a certain way.
Note that the playbook runs once for all of the sandbox's Apps that use that playbook, after CloudShell has finished deploying their VMs.
Depending on the selection, additional options may become available.
Connection Method The method to use to connect to the VM.
Select:
- SSH if the VM has a Linux OS
-
Windows Remote Management if the VM has a Windows OS
Note: To run configuration management on a Windows VM, the VM must have WinRM enabled. For details, see Enable WinRM on Windows VMs to Support Ansible and Enable WinRM on Windows VMs to Support PowerShell Scripts.
Playbook / Script Location Details of the Ansible playbook or custom script.
- URL: URL to the raw version of the Ansible playbook or custom script on the online repository. URL must be accessible to the Execution Servers.
-
User/Password|Token: (For private repositories) Access credentials or token to the script/playbook's online repository.
Notes for Custom Script configurations: In SSH mode, only bash and sh scripts are allowed. In WinRM mode, only PowerShell scripts are allowed.
Notes for Ansible configurations:
The Ansible playbook must be a YML or YAML file. To specify multiple playbooks or a hierarchy of an Ansible project, specify a ZIP package. If a ZIP containing 2 or more playbooks is specified, CloudShell will use the playbook file titled site.yml or site.yaml. If the file is missing, the App's deployment will fail.
Inventory Groups (For Ansible) Specify the host groups for the application to be installed, separated by semicolons (;). The newly deployed VM will be associated to these groups, thus allowing plays that target these groups to run on the VM.
For example:
Servers/AppServers;Servers/DBServersParameters Parameters to be passed to the Ansible playbook or custom script. Specify the parameters and their default values.
In the blueprint or sandbox diagram, privileged users can also set the parameter to receive the value that is specified for a global input when reserving a sandbox containing the App. This is done by selecting the global input when editing the App in the blueprint or sandbox diagram. For example, a global input that specifies the build number of a product to be tested or which components of a product to install.
(For Ansible) To customize the port to be used to communicate with the VM, add the
Ansible_portparameter. Default:SSH/Port: 22/WinRM: 5985.Additional Arguments (For Ansible) Define arguments to be passed to the execution of the playbook (
Ansible-playbookcommand). For example,-vwill set verbose mode on while-fwill set the maximum number of VMs to be handled in parallel. Multiple arguments can be given, separated by spaces. For additional information on possible arguments, see the official Ansible documentation.The arguments must be specified in Resource Manager Client > Configuration Services family > Ansible Configuration model > Ansible Additional Arguments attribute.
Note: The arguments are defined globally for all Apps using Ansible.
Important: To configure Ansible to connect to certified hosts only (Linux VMs with a valid 'known_hosts' key), include the following additional arguments:
--ssh-extra-args='-o StrictHostKeyChecking=yes' -
In the left pane, click App Resource to optionally set the VM's operating system user credentials (for example, to connect to the VM via RDP or SSH). You can also change the deployed App's Shell.
 More...
More...
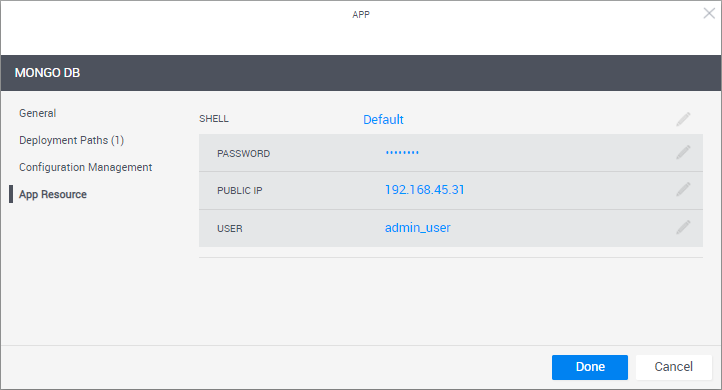
To help sandbox end-users connect to the VM, it is recommended to include the User and Password in the blueprint's instructions. For additional information, see Add Instructions.
Shell The Shell on which the App's VMs are based. When an App is deployed in a sandbox, it changes into a "deployed App resource", which is based on the selected Shell. By default, the "Generic App Model" Shell is used.
Deployed Apps include a default set of commands such as Power On and Refresh IP, and the VM's User and Password attributes, as explained below.
Note: Changing the Shell might cause additional fields to become visible and you may need to enter further information.
User VM's user name
Notes:- Azure VM username and password restrictions apply. For details, see Frequently asked question about Windows Virtual Machines.
- For Azure Marketplace VMs, if the user is not set, CloudShell will set adminuser as the default user name.
- For AWS instances, To support QualiX in-browser connections to AWS instances, make sure to set the credentials of a user that already exists on the Amazon machine image.
Password VM user's password
Notes for Azure Marketplace VMs:- If the password is not set, only the user name will be required. For Linux VMs, CloudShell will create an SSH key-pair to enable a secure connection.
- If the password is set, it will be displayed as asterisks (******) in the blueprint or sandbox.
-
Click Done.
The new App template is displayed in the Apps page.
Cloning App templates
This section explains how to clone an existing App template in the Apps page. You can use this method, for example, if you want to create an App template that is largely based on an existing one but requires several modifications.
To clone an App template:
-
In the Manage dashboard, in the left sidebar, click Apps.
The Apps page is displayed.
-
Click the App template's menu button
 and select Clone.
and select Clone.The cloned App template is added to the Apps page under the original App template. For example:
Editing App templates
This option is enabled using the RestrictEditToCreatingDomain key.
To edit an App template:
-
In the Manage dashboard, in the left sidebar, click Apps.
The Apps page is displayed.
- Click the Name of the App template.
Or-
Click the App template's menu button
 and select Edit.
and select Edit.The App template's configuration wizard is displayed in the General page.
- Edit the App template’s settings. For more information, see Adding App templates.
- Click Save.
Deleting App templates
This option is enabled using the RestrictEditToCreatingDomain key.
To delete App templates:
-
In the Manage dashboard, in the left sidebar, click Apps.
The Apps page is displayed.
- Select the check boxes of the required App templates.
-
Click the Delete button in the toolbar.
Or-
Click the App template's menu button
 and select Delete.
and select Delete.
