Connect Resources and Apps
You can connect and disconnect resources and Apps that are linked by a connection route. For information about connection routes, see Connectivity Overview
In this article:
Viewing connection status
To view the connection status of a connection:
- Click a connection. A context menu is displayed.
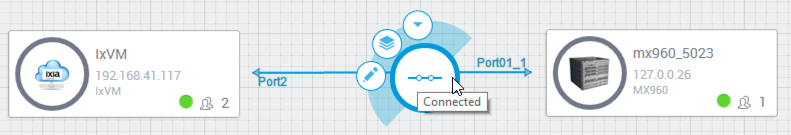
The icon at the center of the menu circle indicates the current state of the route - Connected or Disconnected.
For more details about the connection, from the side-panel, select Properties.
Connecting or disconnecting reserved resources
You can connect or disconnect connections of type Route, Tap, Cable, and Connector (for LAN/Subnet connections). Connecting and disconnecting a connection creates/removes the internal mapping required for the connection.
Note: When reserving a blueprint that has connection routes, the default setup script automatically connects all physical and virtual network connections. And when a sandbox ends, all the route mappings of the sandbox are cleared by the default teardown script. For additional information, see CloudShell Sandbox Template.
To connect or disconnect a reserved route:
- Click a connection.
-
From the Actions context menu, click the appropriate option (Connect or Disconnect).
Note: You cannot connect or disconnect deployed Apps to or from a subnet.
Connecting all endpoints of a VLAN service
It is also possible to connect all endpoints that are connected to a VLAN service using the service's Connect All command.
Note: Subnet services are automatically deployed during the sandbox's setup phase by CloudShell's Default Sandbox Setup script, but do not have a Connect All command.
To connect a VLAN service's endpoints:
- In the sandbox, click the VLAN service.
-
Select Commands.
The Service Commands pane is displayed on the right.
-
Click Connect All.
Note: If the command is missing, ask your administrator to add the VLAN service model to the Vlan Service Connect All script in the Scripts - Resource management page.
Connecting vCenter Apps to an existing VLAN port group
This capability is supported for Apps based on vCenter 2nd Gen shell cloud provider resources.
It is possible to connect an App or deployed App to an existing port group. This enables you to connect deployed Apps in different sandboxes and also to connect Apps deployed in a sandbox to static VMs on the vCenter server. This creates a shared connection, so you can use the same VLAN ID in different blueprints/sandboxes.
Note: This capability is supported only for vCenter Apps and applies to port groups created on the datacenter defined on the vCenter cloud provider resource.
For illustration purposes, the below procedure assumes you want to connect an App to port group "QS_vSwitch1_VLAN_100_Access":
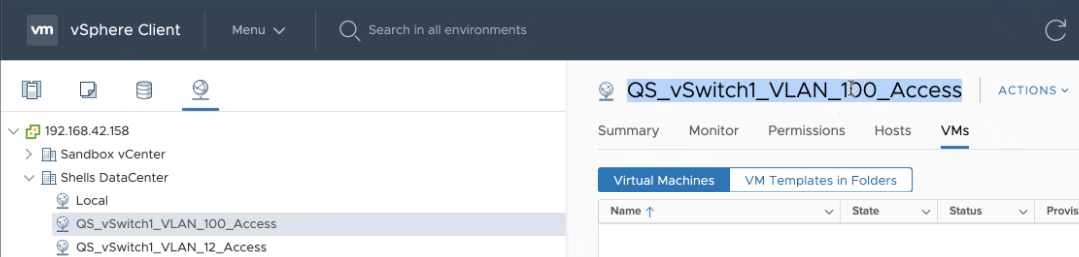
To connect an App to an existing port group:
-
Configure the Virtual Network attribute on the VLAN service as follows:
 To configure the Virtual Network attribute:
To configure the Virtual Network attribute:
- In Resource Manager Client, open the Attributes explorer.
- Edit the Virtual Network attribute.
-
Make sure the Read-only checkbox is unselected.
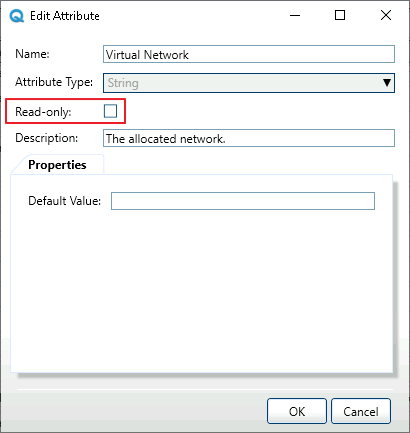
- Click OK and save.
-
Open the Resource Families explorer and expand the Virtual Network family.
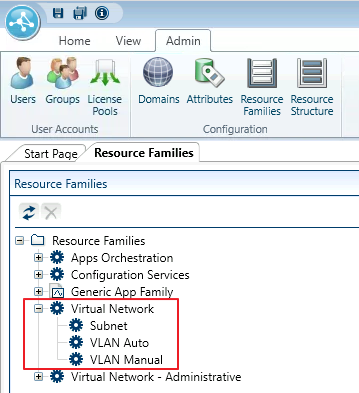
- Click the appropriate service model (VLAN Auto / VLAN Manual).
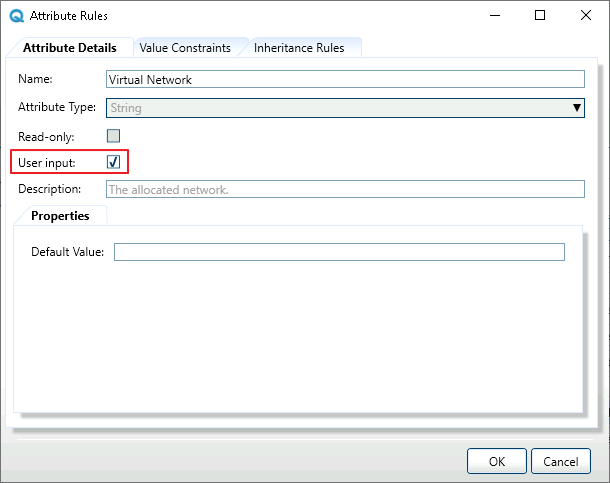
- From the model's Attributes tab, select Virtual Network and click Edit Rules.
-
Select User input and click OK and save.
- Open the blueprint or sandbox.
- From the App / Service pane, drag the VLAN service into the diagram.
-
Set the service's details:
- Virtual Network: Network name or ID in the Virtual Network field. Make sure to specify a value in the VLAN ID field - this will be ignored but it must have a value as it's a system mandatory attribute.
- VLAN ID: Port group's VLAN ID. This VLAN ID will be used if the Virtual Network field is left empty.
Tip: For additional port group configurations, see release 6.0.0 in VMware vCenter.
- Click Add.
- Create connection requirements between the vCenter Apps and the service.
-
Deploy the connection(s), as appropriate.
The connection is created like with any other VLAN service. This includes by deploying the App, connecting the purple Connector line if the App is already deployed, and reserving the blueprint.
Connecting Azure Apps to predefined subnets
This capability is supported for Apps based on Azure 2nd Gen shell cloud provider resources.
It is possible to connect Azure Apps to subnets residing in the Sandbox VNet.
To connect Azure Apps to a predefined subnet:
- Download the Azure.Subnet.zip file from the Azure 2nd Gen shell's Integrations page.
- Import the ZIP file into CloudShell Portal.
- Open the blueprint or sandbox.
- From the App / Service pane, drag the new Azure Subnet service into the diagram.
- Set the following details on the service:
- Public: Subnet's privacy policy - Public to enable connections to the subnet's VMs from outside the subnet or Private.
- Subnet Name: The name of the subnet, as displayed in the Subnets blade on Azure.
- Click Add.
-
Deploy the connection(s), as appropriate.
The connection is created like with any other Subnet service. This includes by deploying the App, connecting the purple Connector line if the App is already deployed, and reserving the blueprint.
Connecting OpenStack App to an existing network
This capability is supported for Apps based on OpenStack 2nd Gen shell version 1.2.0 and up.
This section explains how to enable CloudShell to connect an OpenStack App to an existing network. This capability requires editing the VLAN Auto / VLAN Manual service models in Resource Manager Client.
To allow connecting to an existing VLAN network:
- In Resource Manager Client, open the Attributes explorer.
- Edit the Virtual Network attribute.
-
Unselect the Read-only checkbox and click OK and save.

-
Open the Resource Families explorer and expand the Virtual Network family.

- Click the appropriate service model (VLAN Auto / VLAN Manual).
- From the model's Attributes tab, select Virtual Network and click Edit Rules.
-
Select User input and click OK and save.

-
In the blueprint, add the VLAN service and specify a network name or ID in the Virtual Network field. Make sure to specify a value in the VLAN ID field - this will be ignored but it must have a value as it's a system mandatory attribute.
Note: The network must have a subnet.
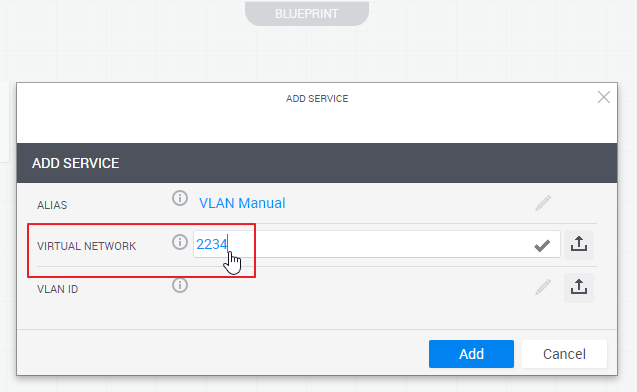
- Click Add.
Specify Subnet CIDR for OpenStack VLAN service
This capability is supported for Apps based on OpenStack 2nd Gen shell version 1.2.0 and up.
This capability requires editing the VLAN Auto / VLAN Manual service models in Resource Manager Client.
To allow connecting to an existing VLAN network:
- In Resource Manager Client, open the Attributes explorer.
-
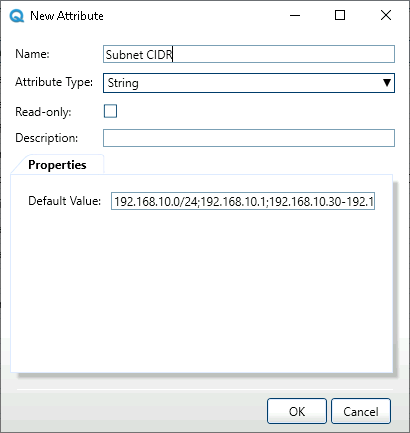
Add a new attribute with the following settings:
- Name: Subnet CIDR
- Attribute Type: String
- Value: CIDR string in the format
CIDR[;Gateway][;First_IP-Last_IP]
For example:
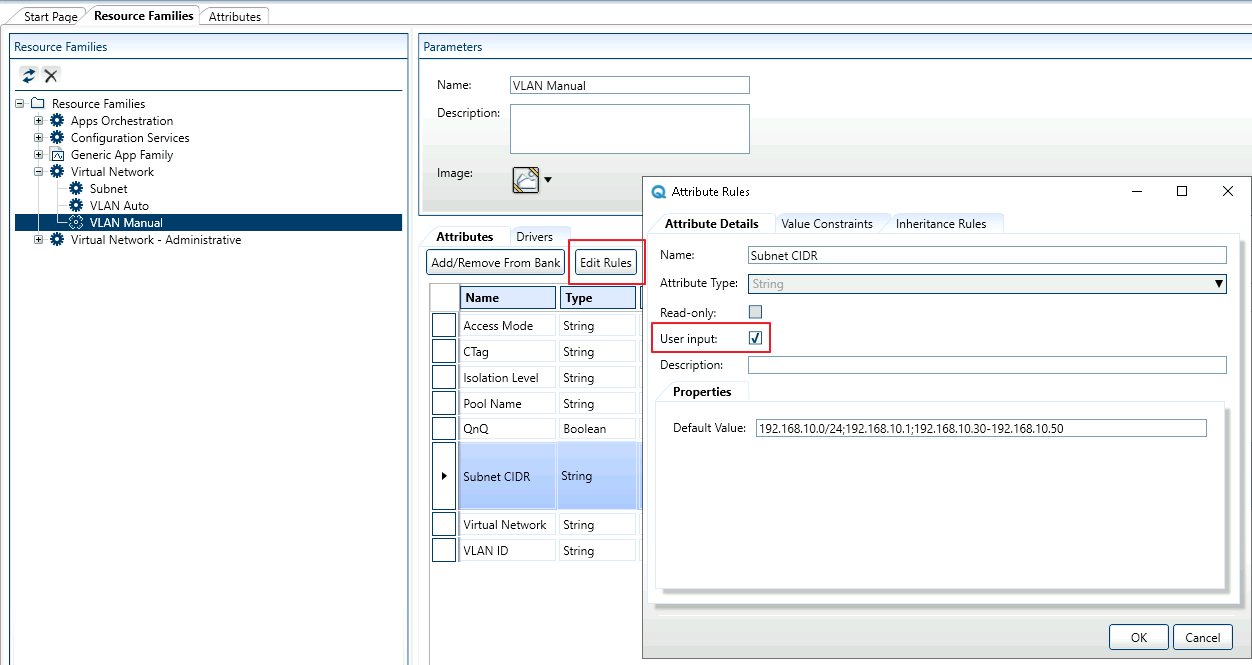
- Open Resource Families > Virtual Networks and add the attribute to the appropriate service model (VLAN Auto / VLAN Manual).
-
To allow the user to set the subnet CIDR, in the service model, select the attribute, click Edit Rules, and make sure User input is selected.
- Save your changes in the Resource Families explorer.
